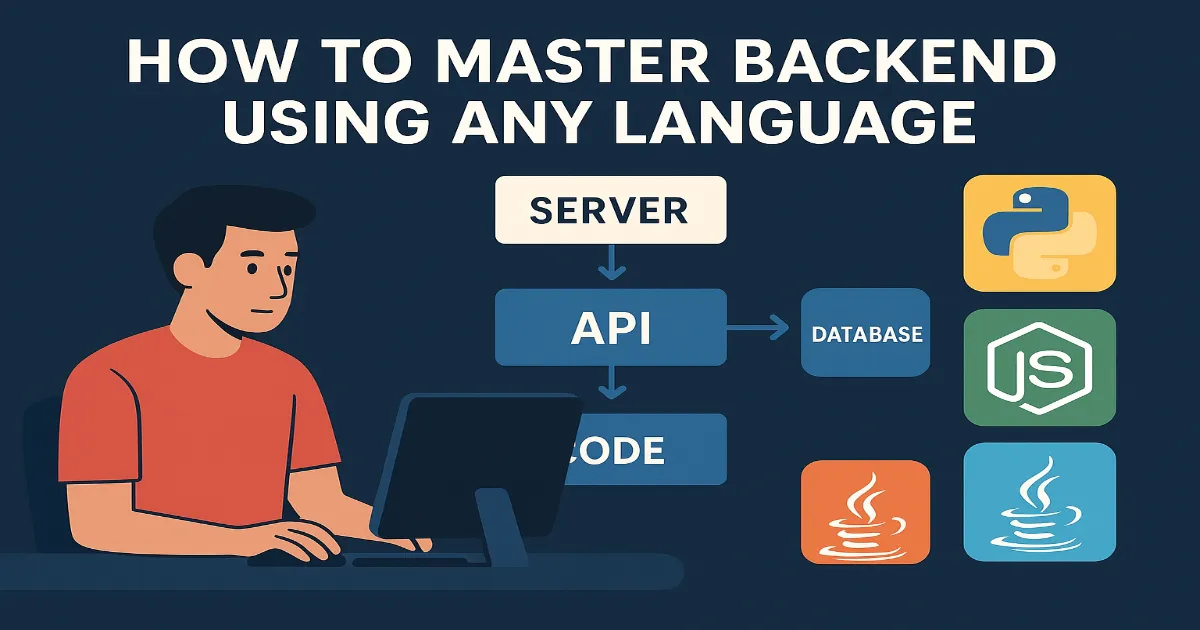
The numbers tell a story that no security leader can afford to ignore. The global cybersecurity workforce shortage now stands at 4.8 million professionals, and the average cost of a single data breach has settled at $4.44 million, a figure that represents not just financial loss, but the compounding damage of slow detection, delayed containment, and eroded trust. As cybersecurity awareness continues to surge as a national priority, organizations are realizing that awareness alone cannot close the gap. The structural answer is automation: the systematic replacement of manual, repetitive security tasks with machine-speed processes that operate continuously and at scale.
- What Is Cybersecurity Automation and Why Does It Matter Now?
- The Core Cybersecurity Automation Tools You Need to Know
- How Does Cybersecurity Automation Actually Work?
- Cybersecurity Automation with Python — A Developer’s Perspective
- What Frameworks Guide Cybersecurity Automation?
- The Business Case — ROI and Benefits of Automating Security
- Cybersecurity Automation Jobs and Career Opportunities
- The Road Ahead: Automation as Infrastructure, Not Optional
This guide breaks down what cybersecurity automation actually looks like in practice, the tools that power it, the frameworks that govern it, the developer workflows that build it, and the business case that justifies it. Whether you are evaluating platforms, building custom scripts, or positioning your career in this space, the information ahead gives you a grounded, data-backed understanding of where automation stands in 2026.
What Is Cybersecurity Automation and Why Does It Matter Now?
Cybersecurity automation refers to the use of technology, primarily software platforms, scripting, and machine learning, to perform security tasks without direct human intervention. This spans everything from log analysis and alert triage to incident containment and vulnerability remediation. The significance lies in the fact that modern threat landscapes generate volumes of data and events that human analysts cannot process in real time. Automation does not replace analysts; it repositions them toward higher-value work by absorbing the repetitive, time-sensitive layer of security operations. From Manual Alerts to Machine-Speed Response
Traditional security operations relied on a cycle that was inherently slow: a system generates an alert, a human reviews it, determines whether it is genuine, and then manually initiates a response. At low threat volumes, this worked. At current volumes, where thousands of cyber attacks occur daily, it creates a bottleneck that attackers exploit directly. Automated systems compress this cycle from hours or days down to seconds. They can correlate signals across endpoints, networks, and cloud environments, filter out false positives, and trigger predefined responses, all without waiting for a human decision at each step. This matters because every undetected day of a breach adds approximately $18,000 in damages, according to industry cost analyses.
The Workforce Gap That’s Forcing the Shift
The talent shortage in cybersecurity is not a temporary imbalance it is a structural condition. Organizations that are understaffed face breach costs that run $1.76 million higher than their adequately staffed counterparts, per IBM’s cost-of-breach research. This creates a direct financial incentive to invest in automation as a force multiplier. Security teams do not need more bodies on every shift; they need systems that handle volume so that the people they do have can focus on threat hunting, strategy, and incident investigation.
The Core Cybersecurity Automation Tools You Need to Know
The automation layer in modern security operations is not a single product. It is an ecosystem of platforms, each designed to handle a specific function within the detection-and-response chain. Understanding how these security automation tool categories fit together is essential for anyone evaluating or building within this space.
SOAR Platforms — The Orchestration Layer
SOAR stands for Security Orchestration, Automation, and Response. These platforms connect disparate tools — firewalls, endpoint sensors, threat intelligence feeds into a coordinated system. The core mechanism is the playbook: a predefined set of automated actions that execute when specific conditions are met. When a SIEM flags unusual login activity from multiple geographies, a SOAR playbook can automatically enrich that alert with threat intelligence, disable the user account, and open a ticket in the incident management system, all without manual intervention. Gartner’s 2025 Hype Cycle moved standalone SOAR out of the active category not because the function has disappeared, but because it has been absorbed into next-generation platforms like XDR as a native capability.
SIEM Systems — Centralized Detection at Scale
SIEM, or Security Information and Event Management, is the data aggregation and analysis backbone of automated security. It ingests logs from firewalls, servers, applications, and network devices, normalizes them into a common format, and applies correlation rules to surface actionable alerts. The value of SIEM is in its ability to connect signals across an organization’s entire infrastructure: a login anomaly in isolation is noise, but the same anomaly correlated with unusual data movement and a known threat signature becomes a high-confidence detection. This correlation function is what makes SIEM the essential input layer for automation workflows.
XDR and EDR — Endpoint and Extended Detection
Extended Detection and Response platforms represent the next evolution in automated threat detection. Unlike SIEM, which relies primarily on log data, XDR correlates telemetry from endpoints, networks, cloud environments, and email into a unified detection surface. This approach directly reduces alert fatigue a persistent challenge in security operations, by filtering out noise and surfacing only the signals that warrant investigation. XDR platforms also deliver native response actions, such as isolating compromised endpoints or revoking credentials, without requiring a separate orchestration layer. For organizations that rely on DDoS-protected and multi-layered hosting infrastructure, XDR adds an important layer of visibility into how threats move across the perimeter in real time.
How Does Cybersecurity Automation Actually Work?
The mechanics of cybersecurity automation are less about any single technology and more about the structured flow from detection to response. Understanding this flow and how each component connects to the next positions organizations to build automation that is both effective and maintainable.
The Playbook-Driven Incident Response Model
Playbooks are the decision logic of cybersecurity automation. Each playbook maps a category of threat or event to a specific sequence of actions. A phishing detection playbook, for example, executes a chain of steps the moment the trigger condition is met:
- Isolate the affected endpoint — cut it from the network to prevent lateral movement before the threat is fully understood.
- Quarantine the email organization-wide — remove the malicious message from every inbox it reached, not just the original recipient.
- Extract indicators of compromise — pull the IOCs (malicious URLs, file hashes, sender metadata) so they can be fed back into detection rules automatically.
- Notify the security team — flag the incident for human review, but only after the automated steps have already contained the damage.
The strength of this model is consistency: every incident of a given type receives the same structured response, reducing the risk of human error and ensuring that no step is skipped under pressure. The challenge is in the tuning of playbooks that are too broad to generate false positives, while playbooks that are too narrow miss novel attack patterns. This is why MTTD and MTTR have become the gold-standard KPIs for measuring the effectiveness of automated incident response.
Alert Triage, Enrichment, and Automated Correlation
Before a playbook fires, the alert itself must be validated and enriched. Automated triage systems score incoming alerts based on severity, context, and historical patterns, routing high-confidence threats to immediate response and low-confidence signals to a review queue. Enrichment adds depth: an alert about a suspicious IP address gets cross-referenced against threat intelligence databases, geolocation data, and the organization’s own asset inventory all automatically. This enrichment step is what separates noise from signal at scale, and it is where AI-powered breach detection delivers its clearest value. Organizations using AI-driven security systems identified breaches 108 days faster than those relying on traditional methods, translating to an average cost reduction of 43% per incident.
Building from the ground up? If you are still developing your foundational understanding of cyber threats before diving into automation workflows, start with Why Cybersecurity Awareness Is Trending it covers the threat landscape context that makes everything in this guide click.
Cybersecurity Automation with Python — A Developer’s Perspective
Among programming languages, Python occupies a dominant position in security automation due to its readability, extensive library ecosystem, and rapid prototyping capability. The SANS Institute’s SEC573 course positions Python as the backbone of modern infosec automation, covering everything from log parsing to network packet analysis to forensic artifact extraction.
Why Python Dominates Security Scripting
Python’s advantage in cybersecurity is structural. Security work involves processing large, unstructured datasets, logs, network traffic, vulnerability scan outputs, and making rapid decisions based on pattern recognition. Python’s garbage-collected memory management lets developers focus on logic rather than low-level resource handling, and its interpreted execution model makes debugging straightforward in fast-paced incident response scenarios. Its integration capabilities are equally strong: Python scripts can connect to SIEMs, threat intelligence APIs, cloud platforms, and internal databases through well-maintained libraries, turning a single script into a component of a larger automation pipeline. The Axonius Python security workflow outlines a practical five-step process from identifying a use case to testing the output that security teams use to move from concept to production-ready automation.
Key Libraries and Real-World Use Cases
The Python libraries that matter most in cybersecurity automation fall into three categories. Network analysis tools like Scapy enable packet-level inspection and intrusion detection scripting. Cryptographic libraries such as PyCryptodome handle encryption, hashing, and secure token generation operations that form the foundation of data protection workflows. Building production-grade implementations of these primitives, hash generators, encoding tools, and token validators is where hands-on security development begins, and it is the exact workflow that informed the security utilities built on NoCostTools.
Machine learning libraries Scikit-learn, TensorFlow, and PyTorch power the anomaly detection and threat classification models that sit inside modern automated security systems. Scikit-learn, in particular, is widely used to build malware detection classifiers that analyze file attributes like size, entropy, and byte frequency to distinguish benign files from threats. Google’s Cybersecurity Certificate includes a dedicated module on automating security tasks with Python, reflecting how central this skill has become in the security professional’s toolkit.
From Micro-Tools to Security Automation: The Developer’s Toolkit
The path from learning security concepts to building production automation often starts with small, focused tools. Password generators, hash checkers, Base64 encoders, and similar utilities are not just educational exercises they are the building blocks of real security workflows. When Neemesh built the security tools suite on NoCostTools, the project covered exactly this range: client-side Password Generators, SHA and MD5 Hash Generators, Base64 encoding and decoding utilities, and developer tools all designed to run without server-side dependencies and zero signup friction.
The modular architecture that underpinned those tools, with each utility as a self-contained, reusable module, mirrors the structure that scales into larger automation systems. NoCostTools achieved a 150% increase in organic traffic within three months by targeting utility search intent with precision, but the technical lesson transfers directly: building security tools in modular, composable units is how developers move from scripts to systems.
What Frameworks Guide Cybersecurity Automation?
Automation without a governance layer is powerful but undirected. The frameworks that guide cybersecurity automation exist to ensure that organizations apply it consistently, measure its effectiveness, and align it with regulatory and risk management requirements.
NIST Cybersecurity Framework 2.0 and the New Cyber AI Profile
The NIST Cybersecurity Framework has long been the reference standard for managing cybersecurity risk across industries. In December 2025, NIST released a preliminary draft of its Cyber AI Profile, a companion document to CSF 2.0 that directly addresses the intersection of artificial intelligence and cybersecurity operations. The profile organizes its guidance around three focus areas: Secure, which covers protecting AI systems themselves; Defend, which shows how AI can enhance detection and response workflows; and Thwart, which addresses strategies for resisting AI-powered attacks. Developed with input from over 6,500 stakeholders, the Cyber AI Profile represents a structural signal that AI-driven automation is no longer an edge case in cybersecurity planning — it is a core governance requirement.
MITRE ATT&CK — Mapping Threats to Automated Responses
MITRE ATT&CK is the industry’s most widely adopted taxonomy for describing how adversaries operate from initial access and execution to lateral movement and data exfiltration. Its value in the context of automation is precise: it provides a shared language for mapping detected behaviors to known attack techniques, which in turn enables playbooks and detection rules to be written against real-world threat patterns rather than abstract scenarios. Security teams that build their automation logic on top of ATT&CK create systems that are both more accurate and more maintainable, because the underlying framework evolves with the threat landscape. Coursera’s Python for Cybersecurity specialization structures its curriculum around MITRE ATT&CK and SHIELD, reflecting how central this mapping has become in developer-facing security automation.
The Business Case — ROI and Benefits of Automating Security
The decision to invest in cybersecurity automation is ultimately a financial one. The data available in 2025 and 2026 makes the ROI calculation straightforward though the execution requires careful planning.
Faster Detection, Lower Breach Costs
The single most decisive metric in the automation ROI conversation is detection speed. IBM’s cost-of-breach research and industry benchmarks paint a clear picture of what automation delivers at scale:
- 108 days faster detection. Organizations using AI-powered security systems identified breaches 108 days earlier than those relying on traditional methods a speed advantage that directly compresses the window in which damage accumulates.
- $1.9 million lower breach cost. Companies with mature AI security and automation reported average breach costs of $3.62 million versus $5.52 million for those without it, with containment times running 80 days shorter.
- 45% reduction in per-record cost. Automated detection brought the per-record breach cost down to $128, compared to $234 under traditional approaches a ratio that compounds across every incident in a given year.
- 43% average cost reduction per incident. The enrichment and correlation layer, where AI-powered systems cross-reference alerts against threat intelligence in real time, is where the largest single cost savings materialize.
How AI-Driven Automation Cuts Manual Workload by 60–80%
The workload reduction from automation is substantial across every function it touches: alert triage, log analysis, vulnerability scanning, and initial incident response are the highest-impact areas. IBM reports that 51% of enterprises now use security AI or automation, and those organizations experience $1.8 million lower average breach costs. 74% report positive ROI within the first year, rising to 88% among early adopters. The AI-driven security automation savings documented across enterprise deployments consistently show that the highest-value automation is not the most complex it is the most consistently applied.
Cybersecurity Automation Jobs and Career Opportunities
The workforce gap that drives investment in automation also creates a career opportunity for professionals who understand how to build, deploy, and manage automated security systems. This is one of the faster-growing segments in the broader technology job market.
Roles That Are Surging in Demand
Security automation engineers, SOC analysts with automation skills, and cloud security architects represent the three highest-demand roles in this space. These positions require a blend of technical depth, scripting, platform configuration, threat detection logic, and operational judgment about when automation should act and when a human decision is needed. The overlap with entry-level AI career paths is significant: many organizations are building teams that combine AI engineering skills with cybersecurity domain knowledge, creating roles that did not exist five years ago. Cybersecurity automation represents one of the clearest paths to both specialization and salary growth a dynamic confirmed by the fact that cybersecurity ranks among the highest-paying skills in 2026.
Skills and Certifications to Build Your Path
The technical foundation for a career in cybersecurity automation rests on three pillars, each of which can be built incrementally:
- Scripting proficiency, with Python as the priority. Python is the language the security industry has converged on for automation work, from log parsing to threat classification. Start here, build projects, and ship them.
- Platform fluency across SIEM, SOAR, and XDR. Understanding how these tools work individually is table stakes. The real skill is knowing how to configure, extend, and connect them into a coherent automation workflow.
- Threat framework literacy — MITRE ATT&CK and NIST CSF 2.0. These frameworks are the shared language that security automation runs on. Playbooks, detection rules, and governance decisions all trace back to them.
Certifications that validate these skills include the GIAC Python Coder (GPYC), Google’s Cybersecurity Certificate, and vendor-specific credentials from Palo Alto Networks and CrowdStrike. For those building foundational knowledge, the complete guide to AI tools for beginners provides a solid starting point for understanding the broader ecosystem of tools that intersect with security automation.
The Road Ahead: Automation as Infrastructure, Not Optional
Cybersecurity automation has moved past the point where it needs a business case to justify. Faster detection, lower breach costs, first-year ROI for the majority of adopters, and a workforce shortage that shows no sign of closing position automation as foundational infrastructure. The release of NIST’s Cyber AI Profile and the NIST–MITRE AI Security Center confirm that governance is catching up to capability. For security teams, developers, and executives, the question is no longer whether to automate but how to do so with the precision the threat landscape demands.
Found this guide useful? Share it with your security team or bookmark it for reference. Drop a comment below if you have questions about specific cybersecurity automation tools or workflows.